Most Popular Types of WiFi Cyberattacks
A well-protected network provides us with privacy and security of our data. However, it keeps becoming more and more difficult to keep it safe, and simply using long passwords is not enough. Here are a few ways your WiFi network might be attacked.
Man in the middle
This strategy is a cryptographic attack, based on listening on and modifying information between two parties without their knowledge. The attacker becomes a middleman, pretending to be both the user and the application at the same time in order to steal confidential information. During all that time the user believes he's interacting with the app.
Denial of Service (DoS)
WiFi networks use radio waves, so they are susceptible to a DoS attack. During the procedure, the attacker sends a transmission which distorts the effectiveness of the network or completely prevents it from functioning. Unfortunately it's not possible to completely shield this technology from this sort of assault, however the 802.11 standard made the situation better thanks to implementing protection in form of signal selection, which prevents the same communicates from being recorded.
An interesting solution is to utilize special wall and window paints that are able to prevent WiFi signal from leaving the building. Even more successful are IDS/IPS systems for wireless networks, that allow to either slow down or even completely prevent DoS attacks.
Distributed Denial of Service (DDoS)
This is a version of the DoS attack, which relies on disabling the service or system by using up all available resources. Such an attack is conducted by multiple devices simultaneously. Some of them might act as "zombies", being connected to the internet, but containing a remotely operated software without the owner's knowledge.

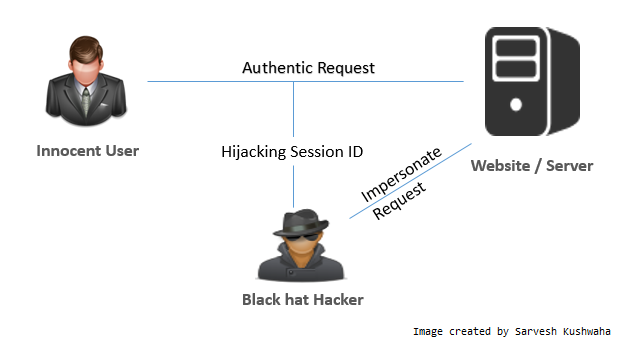
Session Hijacking
Internet portals differentiate between users based on so-called "session IDs", that are placed into cookies and sent to the user in each request after login. So in order to impersonate John Smith on one of the portals we don't need to know his password - it's enough that we have his session ID. How to gather such a cookie? We need to get between John and the service, so for example Facebook. If he's using an open WiFi network, we can use a tool called a sniffer in order to look through his packets and find the information we need.
Get started today & see what your marketing strategy has been missing
- 14 days free
- Easy setup
- Cancel anytime